Prepare for the Worst: Weekend & Vacation Rental Insurance
/in Auto Insurance, Community, Dickey McCay News, Home Insurance, Insurance Agency Near Me, Insurance Agent Near Me, Insurance Tips, Rental Insurance /by Catherine DanglerEveryone looks forward to a fun family vacation during the summer. Some of my best memories from my childhood have been made during vacations and road trips that I have taken with my parents and siblings. There was always so much to look forward to during these trips: fun games during the long car rides, the interesting stops along the way, and even the forced family photos that we could look back on years later. Since this is something near and dear to my heart, I decided recently to buy a second home to rent out as a vacation property; I wanted to help facilitate memorable vacations for other families, just as I had as a child.
Homeowners Insurance Bringing Good Cheer!
/in Dickey McCay News, Home Insurance /by Dickey McCay TeamHomeowners Insurance Protecting All Through the Night!

If you are a new homeowner and are having trouble ciphering through homeowners insurance, you are not alone! In fact, only about half of people who have homeowners insurance claim to fully understand their own policy.
As with most purchases these days, we suggest doing your own research before you settle on a plan. By looking around the web and comparing plans and rates, you will not only have a better understanding for what is best for you, but you can also adjust expectations for what you want your own policy to cover. By having a full understanding of your homeowners insurance, you will feel satisfied and sure when the time comes to get the coverage you need.
Learning the ABCs of Homeowners Insurance
To help you understand homeowners insurance and find the policy that is best for you and your family, we have brought the basics to you.
- What is homeowners insurance?
- In short, homeowners insurance is a type of property insurance that covers private residences by offering financial protection in case of certain types of accidents, burglaries or natural disasters that affect your home. Usually this means that these four aspects are covered: 1) structural damage, 2) personal belongings, 3) liability and 4) additional living expenses.
1) …So What is Structural damage?
- This is one of the key differences between homeowners and renters insurance. Let’s say your condo suffers damage from by burglars or is destroyed by a hurricane, homeowners insurance can cover the costs of repairing, or in some cases even rebuilding it. Your mortgage lender might refer to this as “hazard insurance”, but don’t let that confuse you, this is simply just part of your homeowners policy. We think the best perk of structural damage is that is covers parts of your home that may not even be physically attached to your home, like maybe your shed or garage.
2) What does and does not constitute as “personal belongings”?
Personal belongings that are stolen, damaged, or destroyed by an included disaster on your policy may include:● Clothes
● Furniture
● Appliances
● Computers
● TV and accessories
● Home Decor & Art
● Wine/Spirits
● Sports Equipment
● Toys/Gadgets
● Electronics
●Outdoor Additions (ie, grill, patio furniture, etc.)
Generally speaking, the level of coverage for personal belongings is a percentage of your home’s insured value. For example, if your home is insured up to $200,000, and personal belongings coverage amount is 50% of this, the limit will be $100,000. The actual percentage used varies, however, depending on your policy.
3) What does Liability protection cover?
- Liability protection covers lawsuits against bodily injury or property damage that you, your family and your pets may cause to someone visiting your home. This type of protection typically covers court costs and any awards you may have to pay in court. Your policy should also include Medical Payments Insurance so that if a visitor is hurt at your place of residence, their medical bills can be paid by your insurance company. All of this language and protection can be overwhelming, so when you talk with the experts in the insurance business, you are moving in the right direction toward making sure Liability Insurance protects you.
4) Why would I need additional living expenses in my insurance policy?
- In times of crisis, there will be things you need that you may have not expected. What if your home burnt to the ground? Where would you stay? Under homeowners insurance, your policy would cover the necessary additional living expenses (ALE) when you need to live away from your home. These expenses can include housing, meals, storage fees, etc. And if you rent or do Air BnB for a room or portion of your home, the amount you you would have collected while your home is being repaired will also be covered; win win!
** Note: If you are wondering about Earthquake and/or Flood Insurance, most knowledgeable and experienced insurance agencies can quote and add those coverages either onto your existing policy or a separate policy. When you are thinking about different types of crisis protection, one has to consider earthquake, flood or fire as we have seen devastating damage in the California and some have felt the minor earthquake here in the Tennessee, North Carolina and Georgia Tri-State area.
So what will homeowners insurance NOT cover?- Typical wear and tear
- Damage caused by an earthquake or flood
- Mold caused by high humidity or preventable water leak
How Much Insurance Should I Consider to Protect My Home?

- There isn’t one right answer. But here are a few things to consider when factoring how much coverage you need:
- Current construction costs: In the case your home would have to be completely rebuilt from the ground up, you will need to factor: square footage of your home, type of materials used, special features, and style of your home.
- The value of your personal belongings: To figure out how much coverage you need, conduct a home inventory including:
- Photos of all your belongings
- Write down details of your items (make, model, serial numbers, place of purchase and what you paid)
- Keep receipts and credit card statements
OK. Now I understand what is and isn’t covered in Homeowners insurance policies, but what are the different types of policies?
The different types of policies are known as “forms” and are categorized into the following:
HO-1: Basic policy-The simplest policy; covers 10 specific perils. You may be able to get coverage for belongings inside your home, but it is not offered in many states.
HO-2: Broad policy- Covers all 10 perils included in an HO-1 policy along with an additional six perils. They usually cover not only the structure of your home, but your personal belongings as well. It may also cover liability protection.
HO-3: Special policy- The most common type of policy; provides financial protection from all perils unless noted.
HO-5: Comprehensive policy-Similar to an HO-3 policy, except it offers greater coverage with your belongings and liability protection.
HO-8: Older home policy-This policy is created for older homes where the cost to replace the home is higher than its actual cash value.
How much does homeowners insurance cost?The average annual premium for homeowners insurance in 2015 was $1,173 according to the National Association of Insurance Commissioners (NAIC). However, these costs vary from state to state. For instance, the average premium for a private dwelling in Utah is $673 a year, while in Florida it averages $1,993.
There are myriad factors that affect the overall cost of homeowners insurance:
- Location: Areas that are have a high population density tend to have higher real estate and construction costs, this tends to affects the cost of homeowners insurance.
- Odds of catastrophe. Certain areas in the U.S. are more prone to certain types of catastrophe. For instance, the Carolinas, Florida, and Alabama tend to experience hurricanes which can affects insurance costs.
- Construction costs. The cost of construction depends on the type of residence, how large it is, building materials, building regulations, climate, etc.
● Age of your home
● Square footage of your home
● Construction type
● Number of inhabitants
● Crime in the neighborhood
● Roof type
● Your claim history
● Your credit score
● If you have a home security system in place
● If you have pets
● Your deductible the total amount you’d like covered
Tips on purchasing homeowners insurance- Avoid taking out a policy where claims would be settled by the Actual Cash Value of the items damaged or destroyed. Because of depreciation, the money you receive will generally be less than what you would need to replace items that get damaged.
- Use a local insurance agency. Time and time again we see people simply choosing the cheapest policy without meeting with an agent. Then once they need to be covered, there is no agent they are familiar with and there is no one to fight for their claim. Experts agree your best bet is go with a local company where agents pick up the phone, know your name and policy well, and work hard for you before you need assistance.
- Don’t make claims; if you already have a policy, try to minimize the amount of claims you make. Because this has the potential to increase your premiums so if the amount you claim for is relatively low, you might end up saving money by holding off making a claim and keeping your premiums low.
Insurance can feel confusing and complicated without a professional’s help. We hope we have helped you understand the ins and outs of homeowners insurance. When you feel it is time to get more help, don’t hesitate to reach out to a licensed professional. The agents at Dickey McCay Insuranceare able to communicate the important details that can seem muddled amongst all of the wording and paperwork. Our goal is for you to make an informed decision regarding your policy, potential rates, and every aspect of coverage across many companies. We can help you meet all your insurance needs in a one-stop shop at Dickey McCay Insurance!
Computer Security
/in Cyber Insurance, Home Insurance, Technology News /by Dickey McCay TeamARE YOU PRACTICING GOOD COMPUTER HYGIENE?
 All of us are painfully aware of the online data breaches that occur with alarming frequency. No need to list them here – it would take this entire blog and then some. Most of these breaches that make headlines happen to large retail chains and government agencies – anywhere there are millions of people’s data stored in one place. That does not mean, however, that there is nothing individuals can do to keep themselves as protected as possible.
All of us are painfully aware of the online data breaches that occur with alarming frequency. No need to list them here – it would take this entire blog and then some. Most of these breaches that make headlines happen to large retail chains and government agencies – anywhere there are millions of people’s data stored in one place. That does not mean, however, that there is nothing individuals can do to keep themselves as protected as possible.
For your family, some of our homeowners’ insurance policies include identity-theft coverage, which may include credit monitoring and assistance if your identity is stolen. Prevention, of course, is the best protection so it is crucial that one practice sound “computer hygiene,” by keeping anti-virus software up-to-date, creating unique passwords and changing them periodically and never opening suspicious emails.
For businesses, sound computer hygiene is more complicated. Here’s why.
While it is true hackers go after the “big fish,” they also look for softer targets – smaller businesses with weaker defenses. The most vulnerable businesses are those that accept credit cards, store customer information, and conduct business online or in the cloud.
Cyber Insurance for Safety & Security
For these businesses, it is wise to look into adding cyber and privacy insurance protection to cover liability for a data breach in which the firm’s customers’ personal information is exposed or stolen. These policies cover a variety of expenses, including notification costs, credit monitoring, costs to defend claims by state regulators, fines and penalties, and loss resulting from identity theft. The policies can also cover liability from website media content and other risks from business interruption, data loss/destruction, computer fraud, funds transfer loss and cyber extortion.
One final note: Not all computer hygiene is high-tech. In a small business, every employee wears several hats so it’s important to have strict rules about handling customer data. What would happen if an employee discarded sensitive information into the dumpster by accident or an employee lost their laptop with all their information? A shredder could be a wise investment.
Home Flooding
/in Flood Insurance, Home Insurance /by Dickey McCay TeamIS YOUR HOME FLOOD RESILIENT?
With the devastation of recent hurricanes on everyone’s mind, the dangers of flooding has taken on new urgency. Few of us think want to think about it happening in our backyards. Instead “out of sight, out of mind” though, a better strategy is “prepare for the worst, hope for the best.” Many agencies maintain checklists on what to do before and after a flood, including:
American Red Cross (http://www.redcross.org/get-help/how-to-prepare-for-emergencies/types-of-emergencies/flood)
Federal Emergency Management Agency ( https://www.fema.gov/media-library-data/1409002852888-3c5d1f64f12df02aa801901cc7c311ca/how_to_prepare_flood_033014_508.pdf)
Department of Homeland Security (https://www.ready.gov/floods
Many of us likely sought them out when we thought we might get a direct hit from Hurricane Irma. As good as those checklists are, however, we’d like to suggest one more with steps you can take to reduce the damage to your home in the event of a flood. It comes from the Institute for Business and Home Safety, a non-profit group supported by the insurance industry that does for buildings the same thing that the Insurance Institute for Highway Safety does for cars (crash tests.)
A detailed list is available at https://disastersafety.org/flood/reduce-flood-damage-to-homes/, but we want to display a great chart that illustrates these steps.
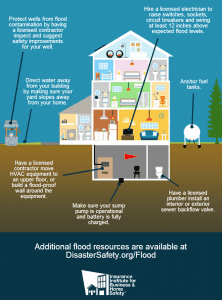
All of us hope that we never to cope with the ravages of a flood, but besides having flood insurance and perhaps a lot of sandbags, there are other steps we can take to keep our prized possessions even safer.
Hours of Operation
Sunday: Closed
Monday: 8:30am – 4:45pm
Tuesday: 8:30am – 4:45pm
Wednesday: 8:30am – 4:30pm
Thursday: 8:30am – 4:45pm
Friday: 8:30am – 4:45pm
Saturday: 9:00am – 12:00pm
Contact Us
Phone: 423-496-3366
Toll Free: 855-876-9779
Fax: 423-496-3368
146 Ocoee St.
P.O. Box 1161
Copperhill, Tennessee 37317
